- 您現(xiàn)在的位置:買賣IC網(wǎng) > PDF目錄4069 > CS80C286-12 (Intersil)IC CPU 16BIT 5V 12.5MHZ 68-PLCC PDF資料下載
參數(shù)資料
| 型號(hào): | CS80C286-12 |
| 廠商: | Intersil |
| 文件頁(yè)數(shù): | 14/60頁(yè) |
| 文件大小: | 0K |
| 描述: | IC CPU 16BIT 5V 12.5MHZ 68-PLCC |
| 標(biāo)準(zhǔn)包裝: | 126 |
| 處理器類型: | 80C286 16-位 |
| 速度: | 12.5MHz |
| 電壓: | 5V |
| 安裝類型: | 表面貼裝 |
| 封裝/外殼: | 68-LCC(J 形引線) |
| 供應(yīng)商設(shè)備封裝: | 68-PLCC(24.23x24.23) |
| 包裝: | 管件 |
第1頁(yè)第2頁(yè)第3頁(yè)第4頁(yè)第5頁(yè)第6頁(yè)第7頁(yè)第8頁(yè)第9頁(yè)第10頁(yè)第11頁(yè)第12頁(yè)第13頁(yè)當(dāng)前第14頁(yè)第15頁(yè)第16頁(yè)第17頁(yè)第18頁(yè)第19頁(yè)第20頁(yè)第21頁(yè)第22頁(yè)第23頁(yè)第24頁(yè)第25頁(yè)第26頁(yè)第27頁(yè)第28頁(yè)第29頁(yè)第30頁(yè)第31頁(yè)第32頁(yè)第33頁(yè)第34頁(yè)第35頁(yè)第36頁(yè)第37頁(yè)第38頁(yè)第39頁(yè)第40頁(yè)第41頁(yè)第42頁(yè)第43頁(yè)第44頁(yè)第45頁(yè)第46頁(yè)第47頁(yè)第48頁(yè)第49頁(yè)第50頁(yè)第51頁(yè)第52頁(yè)第53頁(yè)第54頁(yè)第55頁(yè)第56頁(yè)第57頁(yè)第58頁(yè)第59頁(yè)第60頁(yè)
21
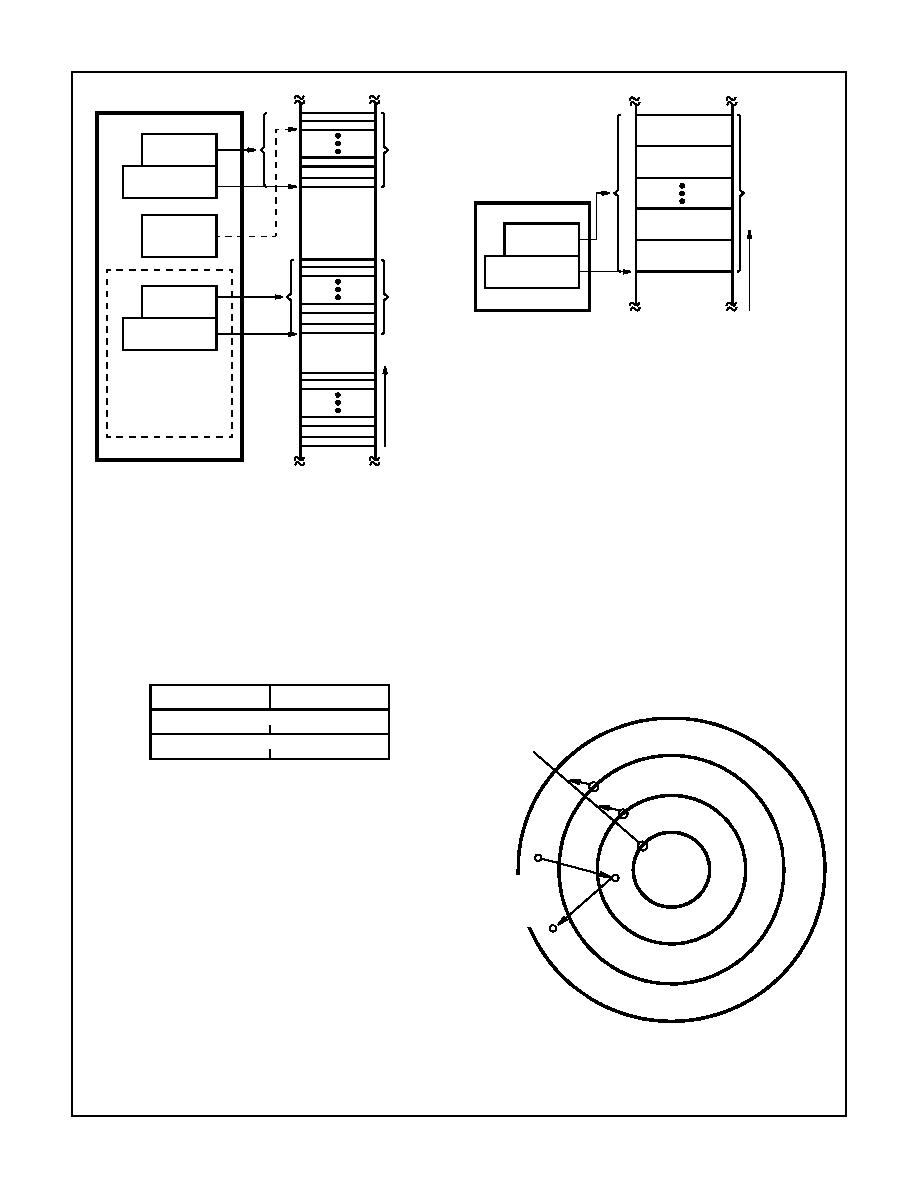
The LGDT and LLDT instructions load the base and limit of
the global and local descriptor tables. LGDT and LLDT are
privileged, i.e. they may only be executed by trusted pro-
grams operating at level 0. The LGDT instruction loads a six
byte field containing the 16-bit table limit and 24-bit physical
base address of the Global Descriptor Table as shown in
Figure 15. The LDT instruction loads a selector which refers
to a Local Descriptor Table descriptor containing the base
address and limit for an LDT, as shown in Table 11.
Interrupt Descriptor Table
The protected mode 80C286 has a third descriptor table,
called the Interrupt Descriptor Table (IDT) (see Figure 16),
used to define up to 256 interrupts. It may contain only task
gates, interrupt gates and trap gates. The IDT (Interrupt
Descriptor Table) has a 24-bit physical base and 16-bit limit
register in the CPU. The privileged LlDT instruction loads
these registers with a six byte value of identical form to that
of the LGDT instruction (see Figure 16 and Protected Mode
lnitialization).
References to IDT entries are made via INT instructions, exter-
nal interrupt vectors, or exceptions. The IDT must be at least
256 bytes in size to allocate space for all reserved interrupts.
Privilege
The 80C286 has a four-level hierarchical privilege system
which controls the use of privileged instructions and access
to descriptors (and their associated segments) within a task.
Four-level privilege, as shown in Figure 17, is an extension
of the users/supervisor mode commonly found in minicom-
puters. The privilege levels are numbered 0 through 3. Level
0 is the most privileged level. Privilege levels provide protec-
tion within a task. (Tasks are isolated by providing private
LDT’s for each task.) Operating system routines, interrupt
handlers, and other system software can be included and
protected within the virtual address space of each task using
the four levels of privilege. Each task in the system has a
separate stack for each of its privilege levels.
Tasks, descriptors, and selectors have a privilege level
attribute that determines whether the descriptor may be
used. Task privilege affects the use of instructions and
descriptors. Descriptor and selector privilege only affect
access to the descriptor.
CPU
GDT LIMIT
GDT BASE
24-BIT PHYS AD
LDT
DESCR
SELECTOR
LDT LIMIT
LDT BASE
24-BIT PHYS AD
PROGRAM INVISIBLE
(AUTOMATICALLY
LOADED
FROM LDT DESCR
WITHIN GDT)
GDT
CURRENT
LDT
INCREAS
ING
MEMO
RY
ADD
RE
SS
MEMORY
LDT1
LDTn
15
0
15
23
15
FIGURE 14. LOCAL AND GLOBAL DESCRIPTOR TABLE
DEFINITION
RESERVED
BASE 15 - 0
LIMIT 15 - 0
15
70 7
7
80
0
+4
+2
0
+5
+3
+1
MUST BE SET TO 0 FOR COMPATIBILITY WITH FUTURE UPGRADES
BASE 23 - 16
FIGURE 15. GLOBAL DESCRIPTOR TABLE AND INTERRUPT
DESCRlPTOR TABLE DATA TYPE
IDT LIMIT
IDT BASE
INTERRUPT
DESCRIPTOR
TABLE
MEMORY
0
15
23
0
GATE FOR
INTERRUPT #n
CPU
GATE FOR
INTERRUPT #1
GATE FOR
INTERRUPT #n-1
GATE FOR
INTERRUPT #0
INCREASING
MEMORY
ADDRES
S
(IDT)
FIGURE 16. INTERRUPT DESCRIPTOR TABLE DEFINITION
APPLICATIONS
OS EXTENSIONS
SYSTEM
SERVICES
KERNAL
PL = 0
MOST
PRIVILEGED
CPU
ENFORCED
SOFTWARE
INTERFACES
HIGH SPEED
OPERATING
SYSTEM
INTERFACE
PL = 1
PL = 2
PL = 3
NOTE: PL becomes numerically lower as privilege level increases.
FIGURE 17. HIERARCHICAL PRIVILEGE LEVELS
80C286
相關(guān)PDF資料 |
PDF描述 |
|---|---|
| IP80C88 | IC CPU 8/16BIT 5V 5MHZ 40-DIP |
| SPC5200CBV400B | IC MPU 32BIT 500MHZ 272PBGA |
| ABB85DHBR | CONN EDGECARD 170PS R/A .050 SLD |
| XF2M-2215-1A | CONN FPC 22POS 0.5MM PITCH SMD |
| MPC859TCVR100A | IC MPU POWERQUICC 100MHZ 357PBGA |
相關(guān)代理商/技術(shù)參數(shù) |
參數(shù)描述 |
|---|---|
| CS80C286-1296 | 制造商:Rochester Electronics LLC 功能描述:- Bulk |
| CS80C286-12X136 | 制造商:Rochester Electronics LLC 功能描述:- Bulk |
| CS80C286-16 | 功能描述:微處理器 - MPU CPU 16BIT 5V CMOS 16 MHZ 68PLCC COM RoHS:否 制造商:Atmel 處理器系列:SAMA5D31 核心:ARM Cortex A5 數(shù)據(jù)總線寬度:32 bit 最大時(shí)鐘頻率:536 MHz 程序存儲(chǔ)器大小:32 KB 數(shù)據(jù) RAM 大小:128 KB 接口類型:CAN, Ethernet, LIN, SPI,TWI, UART, USB 工作電源電壓:1.8 V to 3.3 V 最大工作溫度:+ 85 C 安裝風(fēng)格:SMD/SMT 封裝 / 箱體:FBGA-324 |
| CS80C286-1696 | 制造商:Rochester Electronics LLC 功能描述:- Bulk |
| CS80C286-2 | 制造商:Harris Corporation 功能描述: |
發(fā)布緊急采購(gòu),3分鐘左右您將得到回復(fù)。